This article shows how Fido2 WebAuthn could be used as 2FA and integrated into an ASP.NET Core Identity application. The Fido2 WebAuthn is implemented using the fido2-net-lib Nuget package, and demo code created by Anders Åberg. The application is implemented using ASP.NET Core 3.0 with Identity. For information about Fido2 and WebAuthn, please refer to the links at the bottom.
Code: https://github.com/damienbod/AspNetCoreIdentityFido2Mfa
Creating the ASP.NET Core Application with Identity
The application was created using the ASP.NET Core 3.0 Razor Page template with Identity (Individual User Accounts).
![]()
The following NuGet packages were added. Fido2 is used to implement the Fido2 2FA. Microsoft.AspNetCore.Mvc.NewtonsoftJson is required for the serialization of the Fido requests, responses.
<Project Sdk="Microsoft.NET.Sdk.Web">
<PropertyGroup>
<TargetFramework>netcoreapp3.0</TargetFramework>
<UserSecretsId>aspnet-AspNetCoreIdentityFido2Mfa-590BDC19-E82D-4E23-9F2E-346DA31B5198</UserSecretsId>
</PropertyGroup>
<ItemGroup>
<PackageReference Include="Fido2" Version="1.0.1" />
<PackageReference Include="Microsoft.AspNetCore.Diagnostics.EntityFrameworkCore" Version="3.0.0-preview7.19365.7" />
<PackageReference Include="Microsoft.AspNetCore.Identity.EntityFrameworkCore" Version="3.0.0-preview7.19365.7" />
<PackageReference Include="Microsoft.AspNetCore.Identity.UI" Version="3.0.0-preview7.19365.7" />
<PackageReference Include="Microsoft.AspNetCore.Mvc.NewtonsoftJson" Version="3.0.0-preview7.19365.7" />
<PackageReference Include="Microsoft.EntityFrameworkCore.SqlServer" Version="3.0.0-preview7.19362.6" />
<PackageReference Include="Microsoft.EntityFrameworkCore.Tools" Version="3.0.0-preview7.19362.6" />
<PackageReference Include="Microsoft.Extensions.Logging.Debug" Version="3.0.0-preview7.19362.4" />
<PackageReference Include="Microsoft.VisualStudio.Web.CodeGeneration.Design" Version="3.0.0-preview7-19378-04" />
</ItemGroup>
</Project>
The Identity UI Pages were then scaffolded into the project.
Adding the 2FA using Fido2
Fido2 with the YubiKey 5 Series is used as a 2FA for Identity. For this to work, the user needs to be able to register and activate the Fido2 2FA, then the user can login using the Fido2 2FA and identity. The application also needs a way to deactivate or remove the 2FA.
The demo project from https://github.com/abergs/fido2-net-lib was used to implement the Fido2 logic and also the nuget package. See the docs in the repo.
First the Javascript scripts were added to the wwwroot. mfa.login.js and mfa.register.js plus the 2 required script were added. The scripts were then changed to match the Razor Page templates and the identity requirements.
![]()
These scripts depend on other npm packages, CDNs. These were added to the _Layout.cshtml.
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0" />
<title>@ViewData["Title"] - AspNetCoreIdentityFido2Mfa</title>
<link rel="stylesheet" href="~/lib/bootstrap/dist/css/bootstrap.css" />
<link rel="stylesheet" href="~/css/site.css" />
<link href="https://fonts.googleapis.com/css?family=Work+Sans" rel="stylesheet">
<script src="https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.11.0/umd/popper.min.js" integrity="sha384-b/U6ypiBEHpOf/4+1nzFpr53nxSS+GLCkfwBdFNTxtclqqenISfwAzpKaMNFNmj4" crossorigin="anonymous"></script>
<script type="text/javascript" src="https://cdn.jsdelivr.net/npm/sweetalert2"></script>
<link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/limonte-sweetalert2/6.10.1/sweetalert2.min.css" />
<script defer src="https://use.fontawesome.com/releases/v5.3.1/js/all.js"></script>
</head>
Register Fido 2FA
A Fido2Mfa Razor Page view was created and added to the Identity/Account/Manage folder. The page uses the logged in user. The page can only be accessed when the user has already logged in. The page is used to activate and register the Fido2 device.
@page "/Fido2Mfa/{handler?}"
@using Microsoft.AspNetCore.Identity
@inject SignInManager<IdentityUser> SignInManager
@inject UserManager<IdentityUser> UserManager
@model AspNetCoreIdentityFido2Mfa.Areas.Identity.Pages.Account.Manage.MfaModel
@{
Layout = "_Layout.cshtml";
ViewData["Title"] = "Two-factor authentication (2FA)";
ViewData["ActivePage"] = ManageNavPages.Fido2Mfa;
}
<h4>@ViewData["Title"]</h4>
<div class="section">
<div class="container">
<h1 class="title is-1">2FA/MFA</h1>
<div class="content"><p>This is scenario where we just want to use FIDO as the MFA. The user register and logins with their username and password. For demo purposes, we trigger the MFA registering on sign up.</p></div>
<div class="notification is-danger" style="display:none">
Please note: Your browser does not seem to support WebAuthn yet. <a href="https://caniuse.com/#search=webauthn" target="_blank">Supported browsers</a>
</div>
<div class="columns">
<div class="column is-4">
<h3 class="title is-3">Add a Fido2 MFA</h3>
<form action="/Fido2Mfa" method="post" id="register">
<div class="field">
<label class="label">Username</label>
<div class="control has-icons-left has-icons-right">
<input class="form-control" type="text" readonly placeholder="email" value="@User.Identity.Name" name="username" required>
</div>
</div>
<div class="field" style="margin-top:10px;">
<div class="control">
<button class="btn btn-primary">Add Fido2 MFA</button>
</div>
</div>
</form>
</div>
</div>
</div>
</div>
<script src="~/js/helpers.js"></script>
<script src="~/js/instant.js"></script>
<script src="~/js/mfa.register.js"></script>
The mfa.register.js uses the RegisterFido2Controller to make the Credential Options and to make the Credential. If successful, 2FA is enabled for the Identity using the Identity UserManager.
using System;
using System.Collections.Generic;
using System.Text;
using System.Threading.Tasks;
using Fido2NetLib.Objects;
using Fido2NetLib;
using Microsoft.AspNetCore.Http;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Configuration;
using static Fido2NetLib.Fido2;
using System.IO;
using Microsoft.AspNetCore.Identity;
namespace AspNetCoreIdentityFido2Mfa
{
[Route("api/[controller]")]
public class RegisterFido2Controller : Controller
{
private Fido2 _lib;
public static IMetadataService _mds;
private string _origin;
private readonly Fido2Storage _fido2Storage;
private readonly UserManager<IdentityUser> _userManager;
public RegisterFido2Controller(IConfiguration config, Fido2Storage fido2Storage, UserManager<IdentityUser> userManager)
{
_userManager = userManager;
_fido2Storage = fido2Storage;
var MDSAccessKey = config["fido2:MDSAccessKey"];
var MDSCacheDirPath = config["fido2:MDSCacheDirPath"] ?? Path.Combine(Path.GetTempPath(), "fido2mdscache");
_mds = string.IsNullOrEmpty(MDSAccessKey) ? null : MDSMetadata.Instance(MDSAccessKey, MDSCacheDirPath);
if (null != _mds)
{
if (false == _mds.IsInitialized())
_mds.Initialize().Wait();
}
_origin = config["fido2:origin"];
if(_origin == null)
{
_origin = "https://localhost:44388";
}
var domain = config["fido2:serverDomain"];
if (domain == null)
{
domain = "localhost";
}
_lib = new Fido2(new Fido2Configuration()
{
ServerDomain = domain,
ServerName = "Fido2IdentityMfa",
Origin = _origin,
// Only create and use Metadataservice if we have an acesskey
MetadataService = _mds,
TimestampDriftTolerance = config.GetValue<int>("fido2:TimestampDriftTolerance")
});
}
private string FormatException(Exception e)
{
return string.Format("{0}{1}", e.Message, e.InnerException != null ? " (" + e.InnerException.Message + ")" : "");
}
[HttpPost]
[Route("/makeCredentialOptions")]
public async Task<JsonResult> MakeCredentialOptions([FromForm] string username, [FromForm] string displayName, [FromForm] string attType, [FromForm] string authType, [FromForm] bool requireResidentKey, [FromForm] string userVerification)
{
try
{
if (string.IsNullOrEmpty(username))
{
username = $"{displayName} (Usernameless user created at {DateTime.UtcNow})";
}
var identityUser = await _userManager.FindByEmailAsync(username);
var user = new Fido2User
{
DisplayName = identityUser.UserName,
Name = identityUser.UserName,
Id = Encoding.UTF8.GetBytes(identityUser.UserName) // byte representation of userID is required
};
// 2. Get user existing keys by username
var items = await _fido2Storage.GetCredentialsByUsername(identityUser.UserName);
var existingKeys = new List<PublicKeyCredentialDescriptor>();
foreach(var publicKeyCredentialDescriptor in items)
{
existingKeys.Add(publicKeyCredentialDescriptor.Descriptor);
}
// 3. Create options
var authenticatorSelection = new AuthenticatorSelection
{
RequireResidentKey = requireResidentKey,
UserVerification = userVerification.ToEnum<UserVerificationRequirement>()
};
if (!string.IsNullOrEmpty(authType))
authenticatorSelection.AuthenticatorAttachment = authType.ToEnum<AuthenticatorAttachment>();
var exts = new AuthenticationExtensionsClientInputs() { Extensions = true, UserVerificationIndex = true, Location = true, UserVerificationMethod = true, BiometricAuthenticatorPerformanceBounds = new AuthenticatorBiometricPerfBounds { FAR = float.MaxValue, FRR = float.MaxValue } };
var options = _lib.RequestNewCredential(user, existingKeys, authenticatorSelection, attType.ToEnum<AttestationConveyancePreference>(), exts);
// 4. Temporarily store options, session/in-memory cache/redis/db
HttpContext.Session.SetString("fido2.attestationOptions", options.ToJson());
// 5. return options to client
return Json(options);
}
catch (Exception e)
{
return Json(new CredentialCreateOptions { Status = "error", ErrorMessage = FormatException(e) });
}
}
[HttpPost]
[Route("/makeCredential")]
public async Task<JsonResult> MakeCredential([FromBody] AuthenticatorAttestationRawResponse attestationResponse)
{
try
{
// 1. get the options we sent the client
var jsonOptions = HttpContext.Session.GetString("fido2.attestationOptions");
var options = CredentialCreateOptions.FromJson(jsonOptions);
// 2. Create callback so that lib can verify credential id is unique to this user
IsCredentialIdUniqueToUserAsyncDelegate callback = async (IsCredentialIdUniqueToUserParams args) =>
{
var users = await _fido2Storage.GetUsersByCredentialIdAsync(args.CredentialId);
if (users.Count > 0) return false;
return true;
};
// 2. Verify and make the credentials
var success = await _lib.MakeNewCredentialAsync(attestationResponse, options, callback);
// 3. Store the credentials in db
await _fido2Storage.AddCredentialToUser(options.User, new FidoStoredCredential
{
Username = options.User.Name,
Descriptor = new PublicKeyCredentialDescriptor(success.Result.CredentialId),
PublicKey = success.Result.PublicKey,
UserHandle = success.Result.User.Id,
SignatureCounter = success.Result.Counter,
CredType = success.Result.CredType,
RegDate = DateTime.Now,
AaGuid = success.Result.Aaguid
});
// 4. return "ok" to the client
var user = await _userManager.GetUserAsync(User);
if (user == null)
{
return Json(new CredentialMakeResult { Status = "error", ErrorMessage = $"Unable to load user with ID '{_userManager.GetUserId(User)}'." });
}
await _userManager.SetTwoFactorEnabledAsync(user, true);
var userId = await _userManager.GetUserIdAsync(user);
return Json(success);
}
catch (Exception e)
{
return Json(new CredentialMakeResult { Status = "error", ErrorMessage = FormatException(e) });
}
}
}
}
The RegisterFido2Controller class uses the FidoStoredCredential entity and the Fido2Storage to persist the Fido2 data to the SQL database using Entity Framework Core. The PublicKeyCredentialDescriptor property is persisted as a Json string.
public class FidoStoredCredential
{
public string Username { get; set; }
public byte[] UserId { get; set; }
public byte[] PublicKey { get; set; }
public byte[] UserHandle { get; set; }
public uint SignatureCounter { get; set; }
public string CredType { get; set; }
public DateTime RegDate { get; set; }
public Guid AaGuid { get; set; }
[NotMapped]
public PublicKeyCredentialDescriptor Descriptor
{
get { return string.IsNullOrWhiteSpace(DescriptorJson) ? null : JsonConvert.DeserializeObject<PublicKeyCredentialDescriptor>(DescriptorJson); }
set { DescriptorJson = JsonConvert.SerializeObject(value); }
}
public string DescriptorJson { get; set; }
}
Teh entity is added to the ApplicationDbContext. The Username which is the unique email, is used as a key.
using Microsoft.AspNetCore.Identity.EntityFrameworkCore;
using Microsoft.EntityFrameworkCore;
namespace AspNetCoreIdentityFido2Mfa.Data
{
public class ApplicationDbContext : IdentityDbContext
{
public ApplicationDbContext(DbContextOptions<ApplicationDbContext> options)
: base(options)
{
}
public DbSet<FidoStoredCredential> FidoStoredCredential { get; set; }
protected override void OnModelCreating(ModelBuilder builder)
{
builder.Entity<FidoStoredCredential>().HasKey(m => m.Username);
base.OnModelCreating(builder);
}
}
}
The FidoStoredCredential class can now be used to interact with the database.
using AspNetCoreIdentityFido2Mfa.Data;
using Fido2NetLib;
using Microsoft.EntityFrameworkCore;
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace AspNetCoreIdentityFido2Mfa
{
public class Fido2Storage
{
private readonly ApplicationDbContext _applicationDbContext;
public Fido2Storage(ApplicationDbContext applicationDbContext)
{
_applicationDbContext = applicationDbContext;
}
public async Task<List<FidoStoredCredential>> GetCredentialsByUsername(string username)
{
return await _applicationDbContext.FidoStoredCredential.Where(c => c.Username == username).ToListAsync();
}
public async Task RemoveCredentialsByUsername(string username)
{
var item = await _applicationDbContext.FidoStoredCredential.Where(c => c.Username == username).FirstOrDefaultAsync();
if(item != null)
{
_applicationDbContext.FidoStoredCredential.Remove(item);
await _applicationDbContext.SaveChangesAsync();
}
}
public async Task<FidoStoredCredential> GetCredentialById(byte[] id)
{
var credentialIdString = Base64Url.Encode(id);
//byte[] credentialIdStringByte = Base64Url.Decode(credentialIdString);
var cred = await _applicationDbContext.FidoStoredCredential
.Where(c => c.DescriptorJson.Contains(credentialIdString)).FirstOrDefaultAsync();
return cred;
}
public Task<List<FidoStoredCredential>> GetCredentialsByUserHandleAsync(byte[] userHandle)
{
return Task.FromResult(_applicationDbContext.FidoStoredCredential.Where(c => c.UserHandle.SequenceEqual(userHandle)).ToList());
}
public async Task UpdateCounter(byte[] credentialId, uint counter)
{
var credentialIdString = Base64Url.Encode(credentialId);
//byte[] credentialIdStringByte = Base64Url.Decode(credentialIdString);
var cred = await _applicationDbContext.FidoStoredCredential
.Where(c => c.DescriptorJson.Contains(credentialIdString)).FirstOrDefaultAsync();
cred.SignatureCounter = counter;
await _applicationDbContext.SaveChangesAsync();
}
public async Task AddCredentialToUser(Fido2User user, FidoStoredCredential credential)
{
credential.UserId = user.Id;
_applicationDbContext.FidoStoredCredential.Add(credential);
await _applicationDbContext.SaveChangesAsync();
}
public async Task<List<Fido2User>> GetUsersByCredentialIdAsync(byte[] credentialId)
{
var credentialIdString = Base64Url.Encode(credentialId);
//byte[] credentialIdStringByte = Base64Url.Decode(credentialIdString);
var cred = await _applicationDbContext.FidoStoredCredential
.Where(c => c.DescriptorJson.Contains(credentialIdString)).FirstOrDefaultAsync();
if (cred == null)
{
return new List<Fido2User>();
}
return await _applicationDbContext.Users
.Where(u => Encoding.UTF8.GetBytes(u.UserName)
.SequenceEqual(cred.UserId))
.Select(u => new Fido2User
{
DisplayName = u.UserName,
Name = u.UserName,
Id = Encoding.UTF8.GetBytes(u.UserName) // byte representation of userID is required
}).ToListAsync();
}
}
}
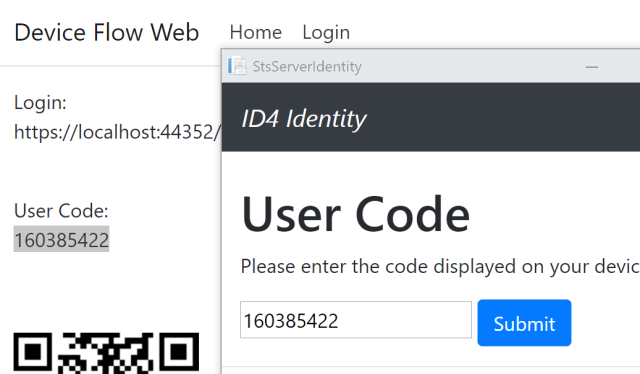
Now the user can register and activate a Fido2 2FA with Identity. Start the application and login. Click your email, and then Two-Factor authentication.
![]()
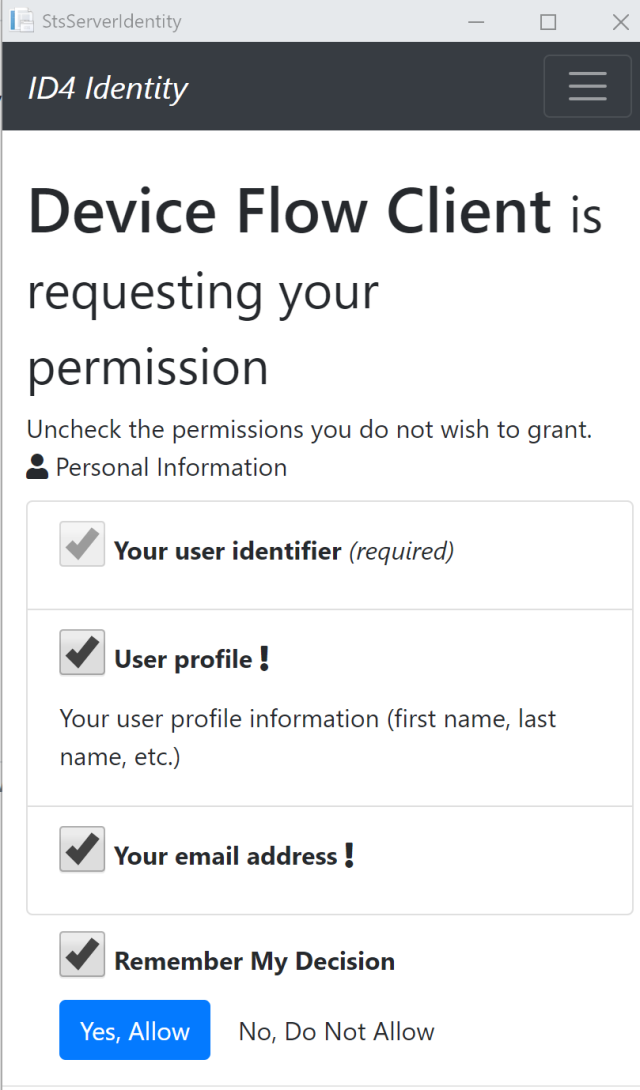
Click Add Fido2 MFA
![]()
Click Add Fido2 MFA. Now you can use your hardware key to complete the request.
![]()
Login with Fido2
The next step is to implement the login with Fido2 2FA. A code if statement to use the Fido 2FA is added to the Account login page. The Fido2Storage instance is added and this is user to check if a Fido2 registration exists for this user. If so, after a successful login, the user is redirected to the second step at the LoginFido2Mfa Razor Page.
using System;
using System.Collections.Generic;
using System.ComponentModel.DataAnnotations;
using System.Linq;
using System.Text.Encodings.Web;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Authentication;
using Microsoft.AspNetCore.Identity;
using Microsoft.AspNetCore.Identity.UI.Services;
using Microsoft.AspNetCore.Mvc;
using Microsoft.AspNetCore.Mvc.RazorPages;
using Microsoft.Extensions.Logging;
namespace AspNetCoreIdentityFido2Mfa.Areas.Identity.Pages.Account
{
[AllowAnonymous]
public class LoginModel : PageModel
{
private readonly UserManager<IdentityUser> _userManager;
private readonly SignInManager<IdentityUser> _signInManager;
private readonly ILogger<LoginModel> _logger;
private readonly IEmailSender _emailSender;
private readonly Fido2Storage _fido2Storage;
public LoginModel(SignInManager<IdentityUser> signInManager,
ILogger<LoginModel> logger,
UserManager<IdentityUser> userManager,
IEmailSender emailSender,
Fido2Storage fido2Storage)
{
_fido2Storage = fido2Storage;
_userManager = userManager;
_signInManager = signInManager;
_emailSender = emailSender;
_logger = logger;
}
public async Task<IActionResult> OnPostAsync(string returnUrl = null)
{
returnUrl = returnUrl ?? Url.Content("~/");
if (ModelState.IsValid)
{
// This doesn't count login failures towards account lockout
// To enable password failures to trigger account lockout, set lockoutOnFailure: true
var result = await _signInManager.PasswordSignInAsync(Input.Email, Input.Password, Input.RememberMe, lockoutOnFailure: true);
if (result.Succeeded)
{
_logger.LogInformation("User logged in.");
return LocalRedirect(returnUrl);
}
if (result.RequiresTwoFactor)
{
var fido2ItemExistsForUser = await _fido2Storage.GetCredentialsByUsername(Input.Email);
if (fido2ItemExistsForUser.Count > 0)
{
return RedirectToPage("./LoginFido2Mfa", new { ReturnUrl = returnUrl, RememberMe = Input.RememberMe });
}
else
{
return RedirectToPage("./LoginWith2fa", new { ReturnUrl = returnUrl, RememberMe = Input.RememberMe });
}
}
if (result.IsLockedOut)
{
_logger.LogWarning("User account locked out.");
return RedirectToPage("./Lockout");
}
else
{
ModelState.AddModelError(string.Empty, "Invalid login attempt.");
return Page();
}
}
// If we got this far, something failed, redisplay form
return Page();
}
}
}
The LoginFido2Mfa Razor Page uses the mfa.login.js to implement the Fido2 logic.
@page
@using Microsoft.AspNetCore.Identity
@inject SignInManager<IdentityUser> SignInManager
@inject UserManager<IdentityUser> UserManager
@model AspNetCoreIdentityFido2Mfa.Areas.Identity.Pages.Account.MfaModel
@{
ViewData["Title"] = "Login with Fido2 MFA";
}
<h4>@ViewData["Title"]</h4>
<div class="section">
<div class="container">
<h1 class="title is-1">2FA/MFA</h1>
<div class="content"><p>This is scenario where we just want to use FIDO as the MFA. The user register and logins with their username and password. For demo purposes, we trigger the MFA registering on sign up.</p></div>
<div class="notification is-danger" style="display:none">
Please note: Your browser does not seem to support WebAuthn yet. <a href="https://caniuse.com/#search=webauthn" target="_blank">Supported browsers</a>
</div>
<div class="columns">
<div class="column is-4">
<h3 class="title is-3">Fido2 2FA</h3>
<form action="/LoginFido2Mfa" method="post" id="signin">
<div class="field">
<div class="control">
<button class="btn btn-primary">2FA with Fido2 device</button>
</div>
</div>
</form>
</div>
</div>
</div>
</div>
<script src="~/js/helpers.js"></script>
<script src="~/js/instant.js"></script>
<script src="~/js/mfa.login.js"></script>
The mfa.login.js script uses the SignInFidoController to complete the login. This controller has two methods, AssertionOptionsPost and MakeAssertion.
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using Fido2NetLib.Objects;
using Fido2NetLib;
using Microsoft.AspNetCore.Http;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Configuration;
using static Fido2NetLib.Fido2;
using System.IO;
using Microsoft.AspNetCore.Identity;
namespace AspNetCoreIdentityFido2Mfa
{
[Route("api/[controller]")]
public class SignInFidoController : Controller
{
private Fido2 _lib;
public static IMetadataService _mds;
private string _origin;
private readonly Fido2Storage _fido2Storage;
private readonly UserManager<IdentityUser> _userManager;
private readonly SignInManager<IdentityUser> _signInManager;
public SignInFidoController(IConfiguration config,
Fido2Storage fido2Storage,
UserManager<IdentityUser> userManager,
SignInManager<IdentityUser> signInManager)
{
_signInManager = signInManager;
_userManager = userManager;
_fido2Storage = fido2Storage;
var MDSAccessKey = config["fido2:MDSAccessKey"];
var MDSCacheDirPath = config["fido2:MDSCacheDirPath"] ?? Path.Combine(Path.GetTempPath(), "fido2mdscache");
_mds = string.IsNullOrEmpty(MDSAccessKey) ? null : MDSMetadata.Instance(MDSAccessKey, MDSCacheDirPath);
if (null != _mds)
{
if (false == _mds.IsInitialized())
_mds.Initialize().Wait();
}
_origin = config["fido2:origin"];
_lib = new Fido2(new Fido2Configuration()
{
ServerDomain = config["fido2:serverDomain"],
ServerName = "Fido2 test",
Origin = _origin,
// Only create and use Metadataservice if we have an acesskey
MetadataService = _mds,
TimestampDriftTolerance = config.GetValue<int>("fido2:TimestampDriftTolerance")
});
}
private string FormatException(Exception e)
{
return string.Format("{0}{1}", e.Message, e.InnerException != null ? " (" + e.InnerException.Message + ")" : "");
}
[HttpPost]
[Route("/assertionOptions")]
public async Task<ActionResult> AssertionOptionsPost([FromForm] string username, [FromForm] string userVerification)
{
try
{
var identityUser = await _signInManager.GetTwoFactorAuthenticationUserAsync();
if (identityUser == null)
{
throw new InvalidOperationException($"Unable to load two-factor authentication user.");
}
var existingCredentials = new List<PublicKeyCredentialDescriptor>();
if (!string.IsNullOrEmpty(identityUser.UserName))
{
var user = new Fido2User
{
DisplayName = identityUser.UserName,
Name = identityUser.UserName,
Id = Encoding.UTF8.GetBytes(identityUser.UserName) // byte representation of userID is required
};
if (user == null) throw new ArgumentException("Username was not registered");
// 2. Get registered credentials from database
var items = await _fido2Storage.GetCredentialsByUsername(identityUser.UserName);
existingCredentials = items.Select(c => c.Descriptor).ToList();
}
var exts = new AuthenticationExtensionsClientInputs() { SimpleTransactionAuthorization = "FIDO", GenericTransactionAuthorization = new TxAuthGenericArg { ContentType = "text/plain", Content = new byte[] { 0x46, 0x49, 0x44, 0x4F } }, UserVerificationIndex = true, Location = true, UserVerificationMethod = true };
// 3. Create options
var uv = string.IsNullOrEmpty(userVerification) ? UserVerificationRequirement.Discouraged : userVerification.ToEnum<UserVerificationRequirement>();
var options = _lib.GetAssertionOptions(
existingCredentials,
uv,
exts
);
// 4. Temporarily store options, session/in-memory cache/redis/db
HttpContext.Session.SetString("fido2.assertionOptions", options.ToJson());
// 5. Return options to client
return Json(options);
}
catch (Exception e)
{
return Json(new AssertionOptions { Status = "error", ErrorMessage = FormatException(e) });
}
}
[HttpPost]
[Route("/makeAssertion")]
public async Task<JsonResult> MakeAssertion([FromBody] AuthenticatorAssertionRawResponse clientResponse)
{
try
{
// 1. Get the assertion options we sent the client
var jsonOptions = HttpContext.Session.GetString("fido2.assertionOptions");
var options = AssertionOptions.FromJson(jsonOptions);
// 2. Get registered credential from database
var creds = await _fido2Storage.GetCredentialById(clientResponse.Id);
if (creds == null)
{
throw new Exception("Unknown credentials");
}
// 3. Get credential counter from database
var storedCounter = creds.SignatureCounter;
// 4. Create callback to check if userhandle owns the credentialId
IsUserHandleOwnerOfCredentialIdAsync callback = async (args) =>
{
var storedCreds = await _fido2Storage.GetCredentialsByUserHandleAsync(args.UserHandle);
return storedCreds.Exists(c => c.Descriptor.Id.SequenceEqual(args.CredentialId));
};
// 5. Make the assertion
var res = await _lib.MakeAssertionAsync(clientResponse, options, creds.PublicKey, storedCounter, callback);
// 6. Store the updated counter
await _fido2Storage.UpdateCounter(res.CredentialId, res.Counter);
// complete sign-in
var user = await _signInManager.GetTwoFactorAuthenticationUserAsync();
if (user == null)
{
throw new InvalidOperationException($"Unable to load two-factor authentication user.");
}
var result = await _signInManager.TwoFactorSignInAsync("FIDO2", string.Empty, false, false);
// 7. return OK to client
return Json(res);
}
catch (Exception e)
{
return Json(new AssertionVerificationResult { Status = "error", ErrorMessage = FormatException(e) });
}
}
}
}
If the Fido2 login is successful, the signInManager.TwoFactorSignInAsync method is used to complete the 2FA in Identity.
This requires an implementation of the IUserTwoFactorTokenProvider to complete the login. The Fifo2UserTwoFactorTokenProvider implements the IUserTwoFactorTokenProvider interface and just returns true.
using Microsoft.AspNetCore.Identity;
using System;
using System.Collections.Generic;
using System.Linq;
using System.Threading.Tasks;
namespace AspNetCoreIdentityFido2Mfa
{
public class Fifo2UserTwoFactorTokenProvider : IUserTwoFactorTokenProvider<IdentityUser>
{
public Task<bool> CanGenerateTwoFactorTokenAsync(UserManager<IdentityUser> manager, IdentityUser user)
{
return Task.FromResult(true);
}
public Task<string> GenerateAsync(string purpose, UserManager<IdentityUser> manager, IdentityUser user)
{
return Task.FromResult("fido2");
}
public Task<bool> ValidateAsync(string purpose, string token, UserManager<IdentityUser> manager, IdentityUser user)
{
return Task.FromResult(true);
}
}
}
For all of this to work, the services and everything needs to be configured in the startup class. The AddControllers method is used to add the services for the Fido2 controllers as well as the extension method AddNewtonsoftJson(). The AddTokenProvider method is used to add the Fido2 2FA provider. Fido2Storage is added as a scoped service.
using System;
using System.Collections.Generic;
using System.Linq;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Builder;
using Microsoft.AspNetCore.Identity;
using Microsoft.AspNetCore.Identity.UI;
using Microsoft.AspNetCore.Hosting;
using Microsoft.AspNetCore.HttpsPolicy;
using Microsoft.EntityFrameworkCore;
using AspNetCoreIdentityFido2Mfa.Data;
using Microsoft.Extensions.Configuration;
using Microsoft.Extensions.DependencyInjection;
using Microsoft.Extensions.Hosting;
namespace AspNetCoreIdentityFido2Mfa
{
public class Startup
{
public Startup(IConfiguration configuration)
{
Configuration = configuration;
}
public IConfiguration Configuration { get; }
// This method gets called by the runtime. Use this method to add services to the container.
public void ConfigureServices(IServiceCollection services)
{
services.AddDbContext<ApplicationDbContext>(options =>
options.UseSqlServer(
Configuration.GetConnectionString("DefaultConnection")));
services.AddDefaultIdentity<IdentityUser>(options => options.SignIn.RequireConfirmedAccount = true)
.AddEntityFrameworkStores<ApplicationDbContext>()
.AddTokenProvider<Fifo2UserTwoFactorTokenProvider>("FIDO2");
services.AddControllers()
.AddNewtonsoftJson();
services.AddRazorPages();
services.AddScoped<Fido2Storage>();
// Adds a default in-memory implementation of IDistributedCache.
services.AddDistributedMemoryCache();
services.AddSession(options =>
{
// Set a short timeout for easy testing.
options.IdleTimeout = TimeSpan.FromMinutes(2);
options.Cookie.HttpOnly = true;
options.Cookie.SameSite = Microsoft.AspNetCore.Http.SameSiteMode.None;
});
}
// This method gets called by the runtime. Use this method to configure the HTTP request pipeline.
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
app.UseDatabaseErrorPage();
}
else
{
app.UseExceptionHandler("/Error");
// The default HSTS value is 30 days. You may want to change this for production scenarios, see https://aka.ms/aspnetcore-hsts.
app.UseHsts();
}
app.UseHttpsRedirection();
app.UseStaticFiles();
app.UseRouting();
app.UseAuthentication();
app.UseAuthorization();
app.UseSession();
app.UseEndpoints(endpoints =>
{
endpoints.MapRazorPages();
endpoints.MapControllers();
});
}
}
}
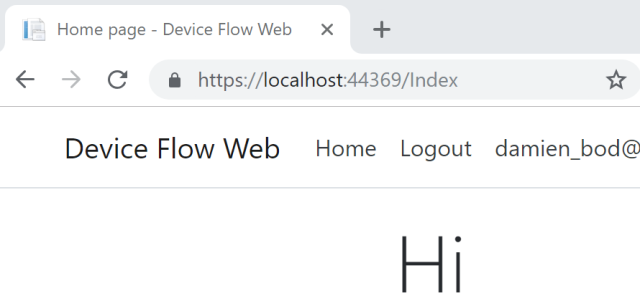
Now that your user is registered, you can click the login button:
![]()
Then the user will be asked to do a second factor auth using the Fido2 device.
![]()
And you can complete the login using the hardware device.
![]()
Disable Fido2 2FA
The identity Disable Razor Page is extended to remove the Fido data for this user.
using System;
using System.Collections.Generic;
using System.Linq;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Identity;
using Microsoft.AspNetCore.Mvc;
using Microsoft.AspNetCore.Mvc.RazorPages;
using Microsoft.Extensions.Logging;
namespace AspNetCoreIdentityFido2Mfa.Areas.Identity.Pages.Account.Manage
{
public class Disable2faModel : PageModel
{
private readonly UserManager<IdentityUser> _userManager;
private readonly Fido2Storage _fido2Storage;
private readonly ILogger<Disable2faModel> _logger;
public Disable2faModel(
UserManager<IdentityUser> userManager,
ILogger<Disable2faModel> logger,
Fido2Storage fido2Storage)
{
_userManager = userManager;
_fido2Storage = fido2Storage;
_logger = logger;
}
[TempData]
public string StatusMessage { get; set; }
public async Task<IActionResult> OnGet()
{
var user = await _userManager.GetUserAsync(User);
if (user == null)
{
return NotFound($"Unable to load user with ID '{_userManager.GetUserId(User)}'.");
}
if (!await _userManager.GetTwoFactorEnabledAsync(user))
{
throw new InvalidOperationException($"Cannot disable 2FA for user with ID '{_userManager.GetUserId(User)}' as it's not currently enabled.");
}
return Page();
}
public async Task<IActionResult> OnPostAsync()
{
var user = await _userManager.GetUserAsync(User);
if (user == null)
{
return NotFound($"Unable to load user with ID '{_userManager.GetUserId(User)}'.");
}
// remove Fido2 MFA if it exists
await _fido2Storage.RemoveCredentialsByUsername(user.UserName);
var disable2faResult = await _userManager.SetTwoFactorEnabledAsync(user, false);
if (!disable2faResult.Succeeded)
{
throw new InvalidOperationException($"Unexpected error occurred disabling 2FA for user with ID '{_userManager.GetUserId(User)}'.");
}
_logger.LogInformation("User with ID '{UserId}' has disabled 2fa.", _userManager.GetUserId(User));
StatusMessage = "2fa has been disabled. You can reenable 2fa when you setup an authenticator app";
return RedirectToPage("./TwoFactorAuthentication");
}
}
}
Add the recovery codes for the Fido2 2FA
The demo code is not complete, the user should be redirected to the generated recovery codes, so if he/she loses the Fido2 hardware device, the account can be recovered.
Hardware
This code and application was tested using YubiKey 5 Series. This works really good, and is only about 50$ to buy. Many online services already support this, and I would recommend this device.
Links:
https://github.com/abergs/fido2-net-lib
The YubiKey
https://www.troyhunt.com/beyond-passwords-2fa-u2f-and-google-advanced-protection/
FIDO2: WebAuthn & CTAP
https://www.w3.org/TR/webauthn/
https://www.scottbrady91.com/FIDO/A-FIDO2-Primer-and-Proof-of-Concept-using-ASPNET-Core
https://github.com/herrjemand/awesome-webauthn
https://developers.yubico.com/FIDO2/Libraries/Using_a_library.html
View at Medium.com
https://docs.microsoft.com/en-us/aspnet/core/?view=aspnetcore-3.0
https://www.nuget.org/packages/Fido2/